Cyber Security Trends
Lintu has development research in cyber trends as follows:

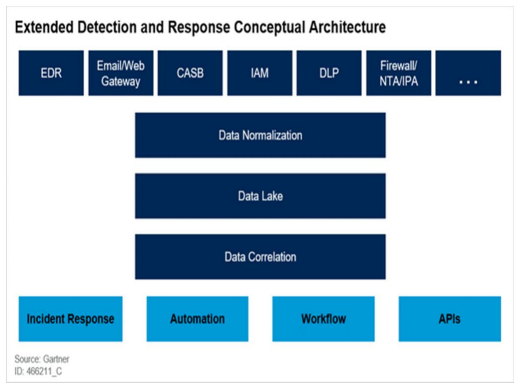
Detection and Response
- Security incident detection and response is the backbone of any security system.
- Emerging technologies such as EDR and XDR serve as platforms that automatically collects and corelates data from multiple security products.
- The goal is protecting end users (your computers, phones, etc.) and the apps and data they consume.
- Technologies such as Symantec DLP scan local hard drives, provide deep visibility into sensitive files that users are storing on their laptops and desktops, and provide local and remote file quarantining responses.
- They also prove protection for inbound data, outbound traffic is also captured and analyzed.
- IBM- QRadar, Cynet- Cynet360, Amazon- AWS, Cisco- Cisco Systems Cloudlock, McAfee- McAfee Vision Cloud all provide automatic detection and correlation of threats, real-time view into data and activity, cross network protection, and automatic response.
- All these make the feat of protecting your network seamless and easy. Some examples of how this will help you:
- For email, protection is deployed at network in/out points, monitor cloud-based email exchange, and is available as software or virtual appliance.
- For Web, it removes sensitive HTML content or blocks requests, integrates with other servers using ICAP, and is available as software/hardware/virtual appliance. For Storage, it will scan network file shares, databases, and other repositories (i.e. local file systems on Windows or Linux).
- For the Cloud, it will provide cloud-to-cloud integration with Symantec CloudSOC, and support for cloud apps (Office 365, G-Suite, Box, Dropbox, and Salesforce).
Automation
- The key to efficiency is automation.
- There are many repetitive tasks associated with keeping a network secure.
- For example, incident response, correlation, remediation and recovery, and detection are the most prevalent.
- However, security process automation hands these tasks over to computer-centric security operations, eliminating the need for human intervention.
- We provide real-time decision making and data capture for ease of detection.
- Our implementation of SOAR tools like User Behavior Analytics (UBA) tracks patterns of human behavior, then applies algorithms and statistical analysis to detect meaningful threats.
- Machine learning and AI technologies will expand the capabilities of your security by adapting to threats that are most common to your network.
- Allowing tasks to be automated can save hundreds of hours of work.
- Shortened threat hunting time will decrease response time.
- Other technologies such as multicloud architecture allows for deployment and management of systems in the cloud as well as on-premises.

- Pre-built workflows and integrations will be aligned to common use cases to further increase efficiency.
- Some candidates include IBM- Cloud Pak for Security, Cisco- SecureX, and Palo Alto-Cortex XDR and Cyberbit- SOC 3D.
- These all provide automatic threat hunting and detection, automatic response and alert, automatic compliance, and integrated machine learning capabilities such as AI.
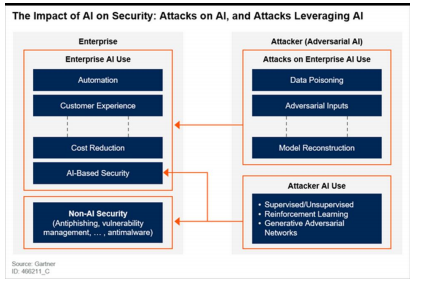
Artificial Intelligence (AI) and Machine Learning
- The automation of repetitive tasks using AI and Machine Learning will increase efficiency of current cyber security processes.
- Certain tasks such as threat detection, data correlation and alerting can all be done without human intervention.
- Not only that, but AI will allow for faster ingesting and processing of data, deeper insight into threats, and extended reach of solutions.
- AI works hand-in-hand with EDR to deliver you with the most seamless cybersecurity protection there is.
- The use of AI and Machine learning will reduce human intervention, reduce operating costs, and improve customer experience.
- However, attackers are implementing new ways to bypass AI security with tactics like phishing and impersonation.
- Machine Learning is useful in this situation because it can adapt to those new threats.
- Not only that, but Machine Learning will learn how to prevent future attacks that are similar.
- Some candidates for this technology include IBM- QRadar, Symantec- Symantec Endpoint Protection 1 and the leader in the financial sector for AI DarkTrace.

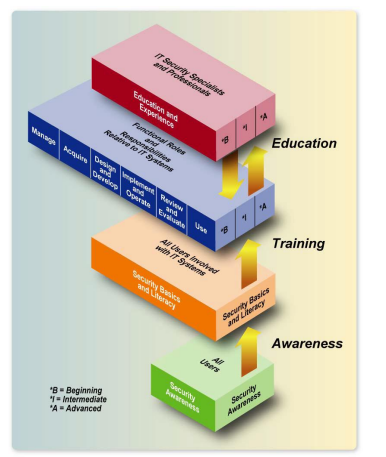
Training
Lintu helps our customer develop a security training program to address commercial and Federal agencies protect the confidentiality, integrity, and availability of information in today’s highly networked systems environment without ensuring that all people involved in using and managing IT:
- Understand their roles and responsibilities related to the organizational mission;
- Understand the organization’s IT security policy, procedures, and practices; and
- Have at least adequate knowledge of the various management, operational, and technical controls required and available to protect the IT resources for which they are responsible.
A successful IT security program consists of: 1) developing IT security policy that reflects business needs tempered by known risks; 2) informing users of their IT security responsibilities, as documented in agency security policy and procedures; and 3) establishing processes for monitoring and reviewing the program.