Critical infrastructures are high value assets (HVAs) that require focused protection. It is compelling therefore to ensure protection of the access to these HVAs, which is achieved through IT endpoints and various interconnected devices constituting the Internet of Things (IoT).
Lintu maintains subscriptions and views into security bulletins, tech advances, and security practice guides, as well as dark web surveillance sources. Using AI and machine learning, we correlate the latest applicability of vulnerabilities and mitigations on behalf of organizations to be able to make focused and relevant protection decisions. The path to HVAs from the innumerable and escalating accrual of edge and mobile devices creates new complexities and expanding forms of risk.

Access is key and must be maintained, but IOT, with often anonymous and unmanaged connectivity, has opened new channels for those perpetrating harm not previously managed with mainstream cyber protection strategies, and a new approach is required to manage this complexity.
- Internet of things (IoT) Cyber Security
- IoT security is the area of endeavor concerned with safeguarding connected devices and networks on the Internet of things (IoT). … IoT products are often sold with old and unpatched embedded operating systems and software.
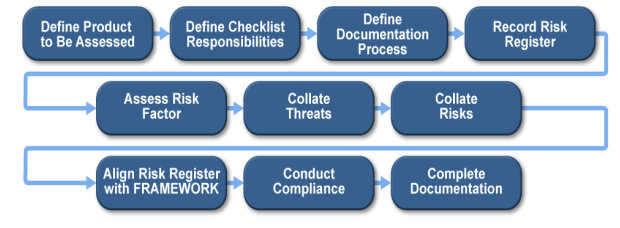
- The core of the security process is understanding what is being protected and from what it is and, is not, being protected. It is recommended to use risk management standards to generate a Risk Register, with which it should be possible to map the features and elements of the product to the requirements of the Framework.