Lintu has extensive experience with federal customers in determining how to implement the NIST Cyber Security Framework. The Framework provides customers with a baseline approach, we help you dive deeper to provide true cyber security not just a checklist.
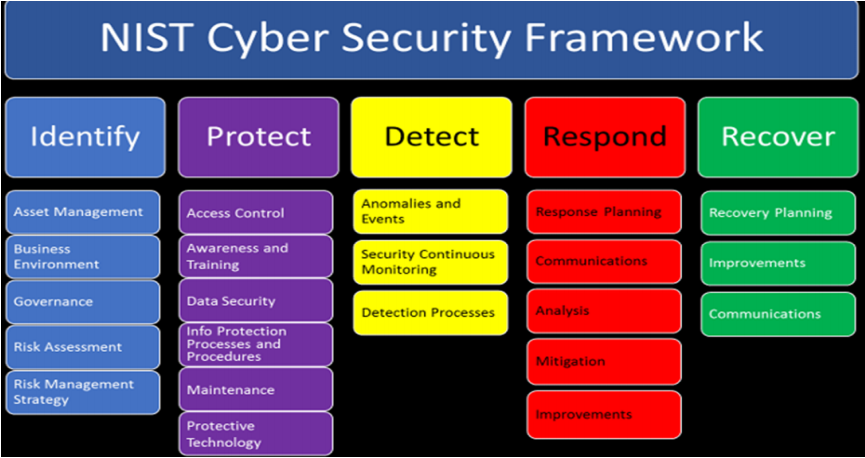
Identify
Planning
- Security Operations Center (SOC) Planning
- Contingency Planning
- Cybersecurity and Privacy in Contractual & Legal Circumstances
- Use of NIST Guidance in Regulatory Settings
- International Alignment Using NIST Guidance
- Cybersecurity Insurance
Risk Assessment
Program Management
- Management/PM Approach
Governance/Change Management
- System and Services Acquisition
Cyber Supply Chain Risk Management
Cloud Implementation Security Consulting
- Cloud Integration
Security Engineering
- Enterprise Identity Management (EIDM)
- IOT security
- Software Assurance and Reliability
SOC Optimization
- SIEM Planning, Implementation and Management
- Vulnerability Management
- Insider Threat Deterrence/Analysis
Human intelligence
Social media security
Security Architecture Optimization
- Segmentation Approach
- Security Orchestration Approaches
- DevSecOps
- Security Automation Adoption Assessments
- Data Encryption Strategies
- Identification and Authentication
Compliance and Authorization
(Added Summary Category)
- Assessment and Authorization (A&A)
- Control Planning and Implementation
- Information Assurance/Enterprise NIST Compliance Support (ISSO)
- Information Assurance/Enterprise NIST Compliance Assessment
- Cloud Compliance – FEDRAMP
- PCI Compliance and Auditing
- GDPR readiness,
- Privacy Consulting/Impact Analysis
Threat Actor Tracking
- Threat Actor Grouping and Type Attribution
Personnel Security
- Identity and Access Management (IDAM)
- Personnel Evaluation
- Physical security controls
- Security awareness and training
Protect
System and Information Integrity
Security Operations Center (SOC) Planning and Operations
- Vulnerability Management
- Patching applications
- Patching operating system vulnerabilities
- Media Protection (maybe?)
Access Control
- Multi-factor authentication
- Enforcing strong passphrase policy
- Disable local administrator accounts
- Restricting administrative privilege strategies
- Restricting access to Server Message Block (SMB) and NetBIOS
- Software-based application firewall, inbound/outbound
- Host-based Intrusion Detection/Prevention System
- Network-based Intrusion Detection/Prevention System
Configuration Management
- Workstation and server configuration management
- Server application configuration hardening
- User application configuration hardening
- Application whitelisting
- Non-persistent virtualized sandboxed trusted operating environment
System and Communications Protection
- TLS encryption strategies between email servers
- Firewall Management (Generous use of term “Firewall”)
- Denying direct Internet access from workstations
- Blocking attempts to access websites by their IP address
- Gateway blacklisting
- Email content filtering
- Blocking spoofed emails
- Web content filtering
- Web domain whitelisting for all domains
- Removable and portable media control
Awareness and Training
- Cyber Cardio for Training
Applied Threat Intelligence
- Phishing Analysis/Mitigation
- Endpoint software using heuristics and automated Internet-based reputation ratings
Physical and Environmental Protection
- Cyber range / test labs, network analysis,
Detect
- CDM Support
- Data Loss Prevention (DLP)
- Signature-based use cases and augmentation
- Host-based Intrusion Detection/Prevention System
- Network-based Intrusion Detection/Prevention System
- Penetration Testing
- Threat Hunting
- Centralized and time-synchronized logging of successful and
failed computer events, and of allowed and blocked network activity - Strategies and use cases for capturing network traffic
- Workstation inspection of Microsoft Office files
Respond
Incident Response
- Incident Management and Forensics
- Real-Time Data Enrichment for incident response and decision support
Audit and Accountability
- Automated dynamic analysis
Malware analytics,
Active Cyber Cardio for Offensive Operations
Recover
- Incident Response (includes recovery)
- Contingency Plan Execution
