- Consolidated, autonomous EPP/EDR
- Network visibility and control over unknown & IoT devices
- Linux, macOS, Windows, Kubernetes, and Docker
- Online/offline protection, detection & response
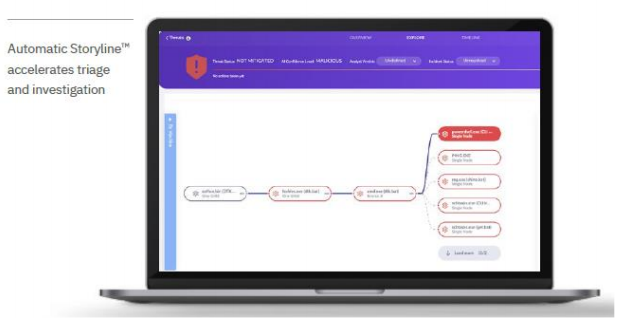
- Automated event correlation into Storylines
- Patented 1-Click Remediation & Rollback
- Full alignment with MITRE ATT&CK® framework
- Flexible EDR data retention, 14-365+ days options

2020 MITRE ATT&CK
- Fewest Misses
- Highest Techniques + Tactics Correlations
- Best Data Enrichment Coverage

2020 FORRESTER WAVETM EDR
Strong Performer

2020 KUPPINGERCOLE MARKET COMPASS
Featured EPDR Innovator
SentinelOne is FedRAMP Authorized at the Moderate+ Impact Level
Robust Forensics, Intuitive Simplicity
EDR can no longer be the exclusive domain of the few. To slash MTTR (Mean Time to Repair) and maximize productivity, EDR 2.0 must simplify detection and response. AI continuously monitors every event, across every OS and every environment, whether data center, cloud service provider, office, or remote work location. Deep Visibility powers hunting and investigation with zero learning curve, bringing IR and hunting to a wider pool of security talent
Key Capabilities
- Autonomous, real-time detection and remediation of complex threats with no need for human intervention
- Uncompromising protection across Windows, Linux, and macOS – physical, virtual, container, cloud, data center, anywhere.
- Accelerated triage and root cause analysis with incident insights and the best MITRE ATT&CK® alignment on the market, with or without MDR. Investigate in seconds with automated correlations and Storylines.
- 1-Click Remediation & Rollback simplifies response and slashes MTTR (Mean Time to Repair).
- Intuitive user experience of Deep Visibility, S1QL, and STARTM (Storyline Active Response) reduces the skills required to add threat hunting to your security operations.
- Data retention options to suit every need, from 14 to 365+ days.
- Rapid deployment interoperability features ensure a fast, smooth rollout.
- Integrated threat intelligence for detection and enrichment from leading 3rd party feeds as well as our own proprietary sources.
SentinelOne NIST RMF
| Function | How SentinelOne can help? | |
|---|---|---|
| Identify | The Identify Function assists in developing an organizational understanding to managing cybersecurity risk to systems, people, assets, data, and capabilities. Understanding the business context, the resources that support critical functions, and the related cybersecurity risks enables an organization to focus and prioritize its efforts, consistent with its risk management strategy and business needs. | SentinelOne is a full feature enterprise-grade EDR platform for use in identifying threats and responding to them. Our EDR is not ordinary. It features high levels of automation to make each analyst’s job easier. SentinelOne also automatically identifies computer assets and users associated with threats in the environment, so that an organization can quickly pinpoint who is affected. |
| Protect | The Protect Function outlines appropriate safeguards to ensure delivery of critical infrastructure services. The Protect Function supports the ability to limit or contain the impact of a potential cybersecurity event. | SentinelOne specializes in protecting Windows, Mac and Linux endpoints and Kuberetes containers from multiple vectors of attack, including file-based malware, script-based attacks, exploits, in-memory attacks, and zero-day campaigns. We achieve this level of endpoint protection with multiple AI models within each agent. SentinelOne convicts and blocks files pre-execution and identifies and kill malicious process on-execution. These multiple protection layers provide a defense-in- depth on every endpoint. |
| Detect | The Detect function defines the appropriate activities to identify the occurrence of a cybersecurity event. The Detect function enables the timely discovery of cybersecurity events. | SentinelOne automatically detects attacks across an organization’s endpoint environment, regardless of how they are delivered to the machine. The agent leverages its multiple detection engines to scan files on write to disk, and model process execution with behavioral AI to detect advanced attacks executing on a system. |
| Respond | The Respond Function includes appropriate activities to take action regarding a detected cybersecurity incident. The Respond function supports the ability to contain the impact of a potential cybersecurity incident. | SentinelOne provides effective response measures through a patented endpoint remediation capability. The SentinelOne agent can automatically clean an infected machine by identifying changes made by malware, and undoing these changes with 1-Click greatly reducing the time to recover from any attack on a machine. |
| Recover | The Recover Function identifies appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity incident. The Recover Function supports timely recovery to normal operations to reduce the impact from a cybersecurity incident. | SentinelOne provides a 1-Click recovery option called Rollback. Rollback will restore a Windows endpoint to a pre-attack state, by not only remediating a machine, but automatically restoring damaged file system info. This feature literally rewinds the effects of attacks such as ransomware, to quickly bring an infected machine back to an operable state. |